
Brocade FCS Fabric - a new generation of Data Center solutions
Brocade Communications Systems as the undisputed leader in the Fiber Channel switch market has introduced solutions from the world of mass storage to a new generation of network switches designed to support Data Centers and private clouds by implementing the VCS Ethernet Fabric technology.
When designing the VCS technology, the needs of customers were taken into account, such as:
- elimination of network barriers in the context of application performance,
- guarantee of service availability in the face of network disruptions and bottlenecks, the need for flexible network scaling with traffic growth and changes in architecture,
- the need to quickly adapt network services to the needs of applications in a private cloud environment,
- simplicity - "is supposed to work" with minimal interference from the administrator,
- support for cloud environments, including renting infrastructure to multiple entities, adjusting policies and automating processes in the cloud.
Compared to the classic hierarchical Ethernet structure, VCS technology provides higher performance, better link utilization, higher reliability and simplicity of architecture.
VCS technology is nothing more than clustering many physical switches to one logical one with all the consequences related to data transmission in the L2 layer inside the cluster. Clustering of switches is possible at distances of up to 200m. However, the specification also provides for clustering over long distances, up to 30km, with some limitations related to the number and type of ports and the availability of technology, in particular FCoE and iSCSI. A VCS cluster is one logical switch from a management point of view.
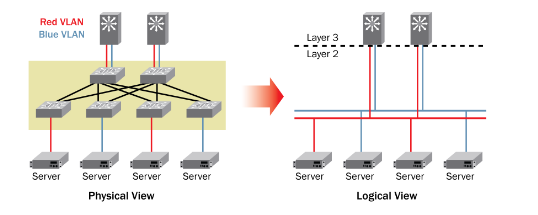
Multiple active data paths are allowed within a cluster. All paths transmit data, and traffic balancing is done for the entire structure at the level of individual packets. This guarantees optimal use of the infrastructure, fast switching in the event of failure of any element of the cluster, and easy scaling. Just add an extra connection and it works. The FCoE protocol is also available inside the entire cluster.
Standard switches and hosts can be connected to the cluster switches by means of multiple aggregated LAG connections without the risk of data loops, without the need to use the STP protocol, with all connections being transmissively active.
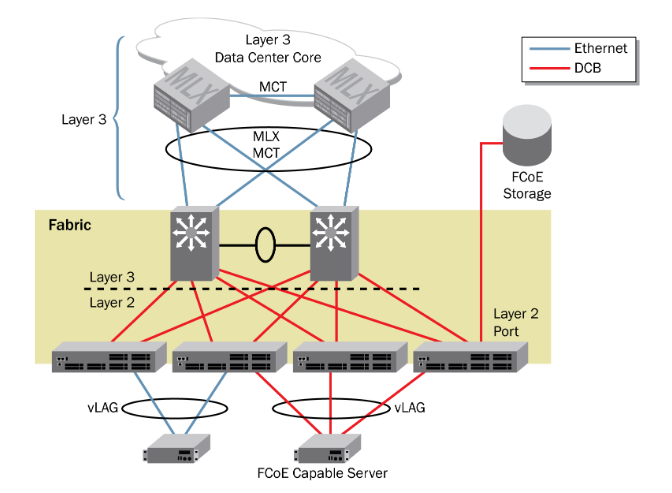
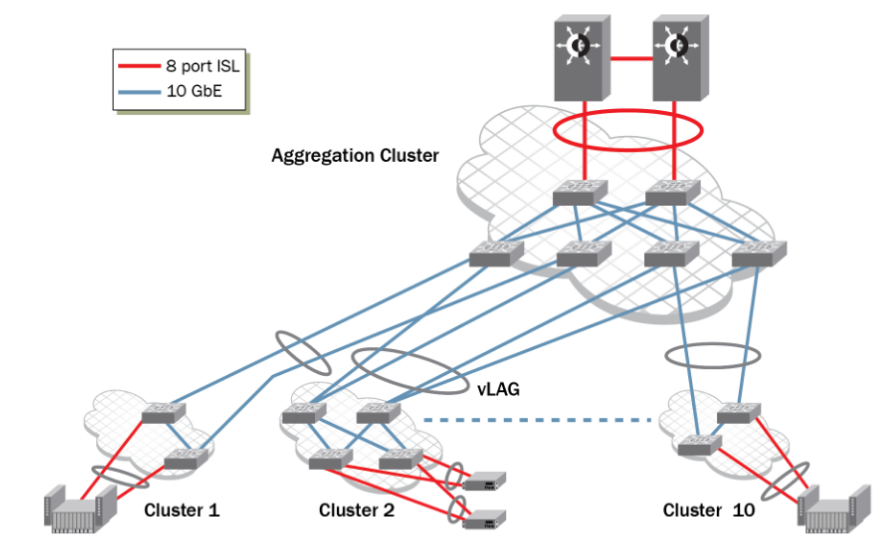
VCS clusters can be combined with each other treating each cluster as a single switch, obtaining a fully reliable, easy to manage, efficient architecture.
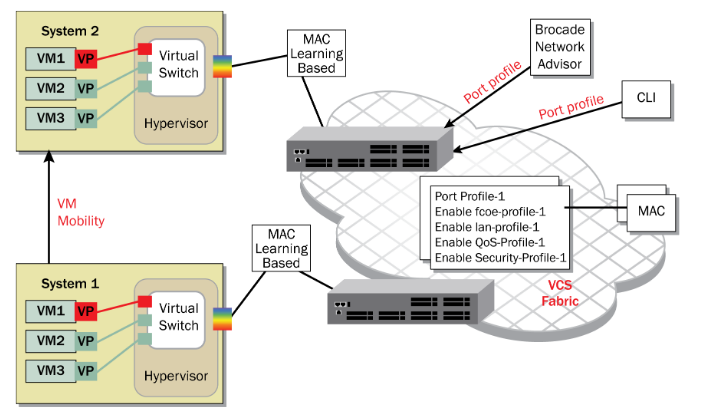
The VCS Fabric solution works with the VMWare environment to offer port profiling. The port profile includes FCoE, VLAN, QoS and security parameters. When migrating a virtual machine between physical hosts, the port profile migrates automatically between cluster switches along with the virtual machine.
Finally, an important point. VCS Fabric technology is available in the entire family of Brocade VDX Data Center Switches at the price of the switch, without additional licenses, and the entire cluster configures itself automatically when data links are connected.




